DeepSound is a sophisticated steganography program designed to conceal multimedia files within audio tracks. This powerful tool provides a secure and user-friendly method for protecting sensitive information by embedding it within seemingly innocuous audio files. This detailed guide explores the functionality, security features, and applications of DeepSound, examining its strengths and potential limitations.
Understanding Steganography and DeepSound’s Role
Steganography, unlike cryptography which scrambles data to make it unreadable, focuses on concealing the very existence of data. DeepSound leverages this principle by embedding files – images, documents, or other data – within the audio data of a chosen carrier file, rendering the hidden information invisible to casual observation. This process makes the existence of secret data extremely difficult to detect, even with basic analysis. The embedded data remains hidden unless extracted using DeepSound itself, thus maintaining its confidentiality.
The software employs advanced techniques to ensure the integrity of both the audio carrier and the hidden file. It carefully integrates the hidden data into the audio stream, minimizing any noticeable degradation in the audio quality. This makes DeepSound particularly useful for situations where maintaining the original audio’s quality is crucial. The technique used prevents discernible artifacts or distortions that might betray the presence of hidden information. DeepSound’s methodology is superior to simpler methods of data hiding which often introduce noticeable noise or distortions into the carrier file, potentially revealing the hidden data.
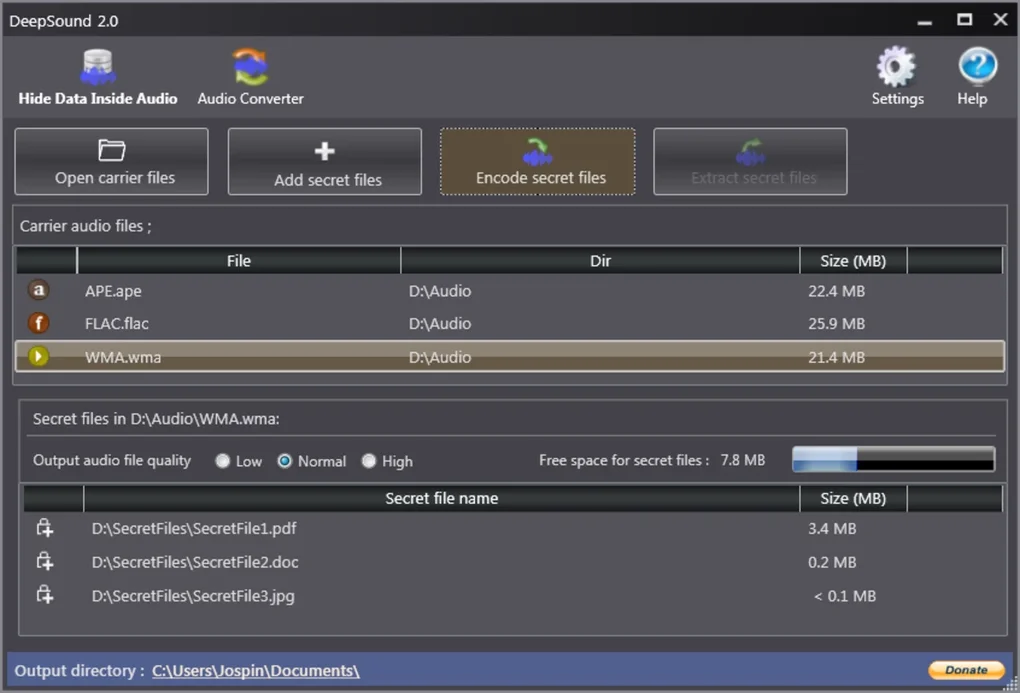
User-Friendly Interface and Functionality
DeepSound boasts an intuitive interface, simplifying the process of hiding and retrieving sensitive data. The process is straightforward, requiring minimal technical expertise. Users begin by selecting an audio file – the carrier – which will house the hidden information. Supported audio formats include common types such as MP3, WAV, FLAC, WMA, and APE, providing users with considerable flexibility in their choice of carrier.
Once the carrier file is selected, users can utilize the “Add secret file” function to embed their chosen data. The software then initiates the steganographic process, integrating the chosen data seamlessly within the audio file’s structure. The progress bar provides visual feedback during the embedding process, allowing users to monitor its completion. Throughout the entire process, the software maintains a focus on user experience, making even complex tasks such as password protection and data selection easy to manage.
Enhanced Security Features: Password Protection and Data Integrity
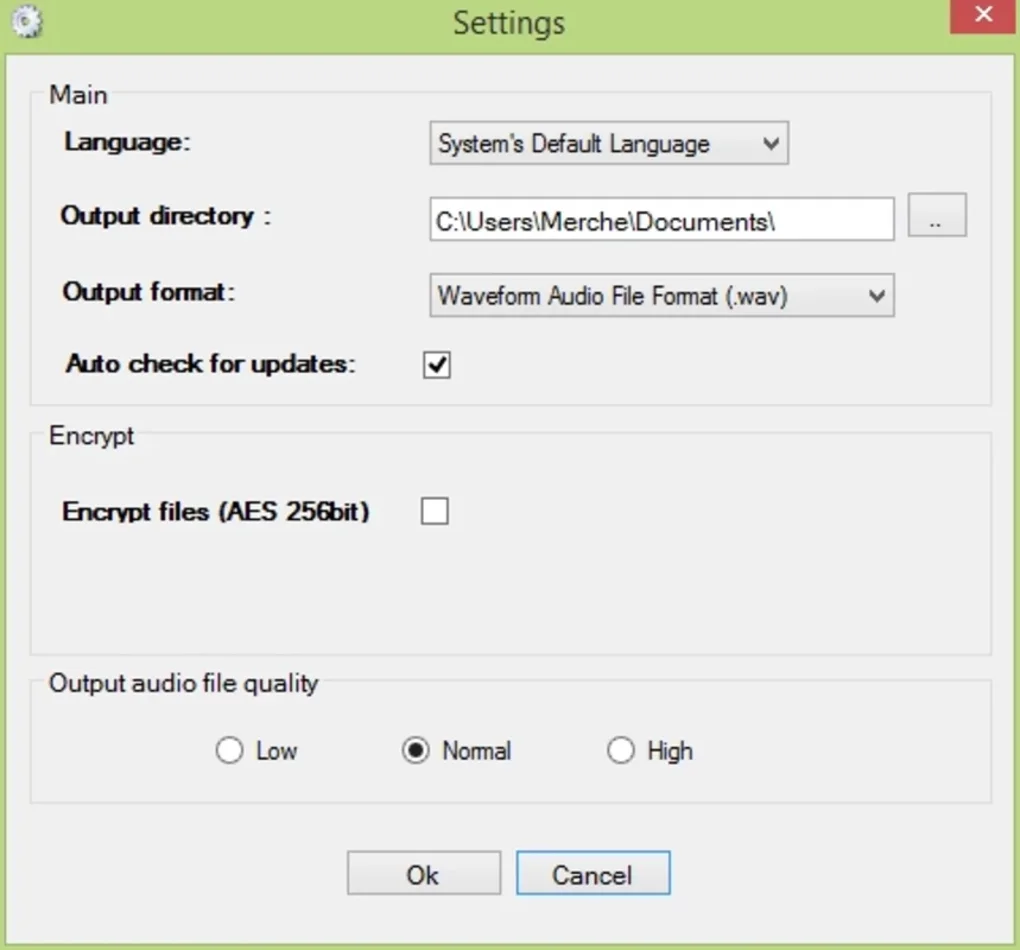
DeepSound prioritizes data security through several key features. One of the most important features is the ability to password-protect the hidden files. This added layer of security ensures that only authorized individuals possessing the correct password can access the concealed information, significantly enhancing the confidentiality of the data. The password protection employs robust encryption algorithms, ensuring the hidden data remains protected even if the carrier file is intercepted.
Beyond password protection, DeepSound’s design incorporates measures to ensure the integrity of the hidden data. The software employs checksums and other verification techniques to detect and prevent any corruption or alteration of the hidden files during the embedding or extraction process. These safeguards ensure that the retrieved data is identical to the original, maintaining its integrity and reliability. The software also includes features to monitor the integrity of the carrier file, ensuring that no inadvertent modifications compromise the hidden data.
Applications and Use Cases
DeepSound’s capabilities extend across a wide spectrum of applications, catering to diverse needs for secure data transmission and storage.
-
Confidential Communication: DeepSound provides a secure way to share sensitive information, such as confidential documents or private communications, without raising suspicion. Embedding this data within an innocuous audio file allows for covert communication, preventing unauthorized access to the information. The recipient, possessing the necessary software and password, can then easily extract the hidden data.
-
Data Backup and Archiving: DeepSound serves as a robust method for creating secure backups of important files. By embedding these backups within audio files, users can create a discreet and easily manageable archive. This method is particularly useful for storing data that needs to remain hidden or for situations where traditional backup methods are impractical.
-
Intellectual Property Protection: For creators and owners of intellectual property, DeepSound provides a way to protect their work from unauthorized access or duplication. Embedding designs, code, or other sensitive data into audio files provides a secure and covert method for storage and transmission.
-
Forensic Investigations: DeepSound’s steganography capabilities could potentially be used by law enforcement or forensic investigators to securely transfer evidence, protecting its integrity and confidentiality during transit.
- Personal Data Protection: Individuals can use DeepSound to protect sensitive personal information, such as financial records, medical data, or identity documents. Embedding this information into audio files provides an additional layer of security, preventing unauthorized access to sensitive details.
Limitations and Considerations
While DeepSound offers a powerful solution for data hiding, it’s important to acknowledge its limitations:
-
Carrier File Size: The size of the audio file limits the amount of data that can be embedded. Larger files allow for more data to be concealed, but this might also increase the chance of detection if the file size change is significant.
-
Detection Methods: Sophisticated steganalysis techniques exist, capable of detecting hidden data in audio files. While DeepSound employs robust techniques to minimize detection, advanced analytical methods could potentially reveal the presence of hidden information. The success of this depends on the sophistication of the detection methods utilized and the specific steganographic techniques applied by DeepSound.
-
Legal and Ethical Considerations: The use of steganography is subject to legal restrictions in some jurisdictions. The use of DeepSound must always comply with applicable laws and ethical guidelines. Using the software for illegal or unethical activities is strictly prohibited.
DeepSound’s Advantages over Other Methods
Compared to other data hiding or encryption methods, DeepSound offers several advantages:
-
Covertness: The hidden data is seamlessly integrated within a common audio file, making it far less suspicious than other methods. Traditional encryption, while secure, often makes the existence of sensitive data immediately apparent.
-
Ease of Use: DeepSound’s user-friendly interface makes it accessible to a broader user base compared to more technically complex encryption methods.
-
Flexibility: The support for various audio formats allows users to choose a carrier file that suits their needs and context.
-
Robust Security: The combination of steganography and password protection creates a highly secure method for data protection.
Conclusion
DeepSound represents a significant advancement in secure data hiding. Its user-friendly interface, robust security features, and wide range of applications make it a valuable tool for individuals and organizations requiring secure data storage and transmission. However, potential users should carefully consider the limitations and legal implications before utilizing this software. Understanding both the capabilities and limitations of the software ensures its responsible and effective use. While no method is completely impenetrable, DeepSound offers a significantly improved level of security compared to many alternative methods, making it a powerful tool in the ongoing battle for data privacy and security.
File Information
- License: “Free”
- Version: “2.0”
- Latest update: “June 17, 2024”
- Platform: “Windows”
- OS: “Windows 11”
- Language: “English”
- Downloads: “868”
- Size: “2.42 MB”
















