iOpus STARR was a Windows-based access control application released in 2005. While no longer actively developed or supported, its historical significance within the context of early internet security and its popularity in specific regions warrants a closer examination. This article delves into the program’s features, its impact, and its place within the broader landscape of computer security software.
iOpus STARR: Functionality and Features
iOpus STARR, short for iOpus Secure Access Restriction and Reporting, was categorized as a security software application specializing in blockers and access control. Its primary function was to restrict access to specific programs, files, or internet resources on a Windows computer. While precise details about its feature set are limited due to the age of the software and the lack of readily available documentation, based on its description and user reviews from the time, we can infer several key functionalities:
-
Program Access Control: The core function involved preventing users from launching specific applications. This could have been achieved through various methods, including file path blocking, registry key manipulation, or process monitoring. This capability was crucial for managing access rights within shared computers or restricting potentially harmful applications.
-
Internet Access Control: iOpus STARR likely included the ability to restrict internet access based on predefined rules or filters. This could have involved blocking access to specific websites or domains, restricting certain types of online activities, or limiting bandwidth usage. Given the prevalence of dial-up and limited bandwidth connections in 2005, this feature would have been highly relevant.
-
Reporting: The name’s inclusion of “Reporting” suggests the software generated logs or reports detailing access attempts, successes, and failures. This functionality would have been valuable for monitoring user activity and identifying potential security breaches.
-
User Management: It is highly probable that iOpus STARR incorporated a basic user management system, allowing administrators to create accounts with different levels of access permissions. This would have allowed for granular control over who could access specific programs or resources on the computer.
The software’s lightweight nature, requiring less storage than average security software of its time, indicates a focus on efficiency and minimal system resource consumption. This was a crucial aspect in the era of less powerful hardware. The relatively small size also suggests a less complex feature set compared to modern, comprehensive security suites.
iOpus STARR: Geographic Reach and User Base
Interestingly, historical data indicates iOpus STARR enjoyed significant popularity in countries such as Cuba, India, and the Czech Republic. The reasons for this regional concentration are speculative but likely stem from a combination of factors:
-
Circumvention of Restrictions: In countries with strict internet censorship or limited access to specific technologies, software like iOpus STARR could have been used to circumvent these restrictions, either by filtering unwanted content or by controlling access to specific applications.
-
Limited Availability of Alternatives: The availability of robust security software might have been limited in these regions due to various factors, including cost, access to international markets, or political considerations. iOpus STARR, being a relatively simpler application, may have filled a gap in the market for basic security functionality.
-
Word-of-Mouth and Local Distribution: The spread of the software could have relied heavily on word-of-mouth recommendations and local distribution networks, leading to concentrated use in particular regions.
The relatively high number of downloads (8,200 in the provided data) considering its age and the limitations of the reporting suggests a substantial user base, particularly within the identified geographic areas. However, the lack of current reviews or usage data prevents a precise assessment of its current relevance.
iOpus STARR: Technical Specifications and Legacy
iOpus STARR was a trialware application, meaning a fully functional version was available for trial, but full functionality likely required a paid license. Its release date of 2005 placed it in a period of significant technological transition in the computer security landscape. The software was compatible with Windows 98 and earlier versions, highlighting its development during a period when these operating systems were still prevalent.
The fact that iOpus STARR remained at version 3.27 and received its last update in September 2005 indicates a cessation of development relatively early in its lifecycle. This lack of updates is a significant factor in its obsolescence. Modern security threats and operating system functionalities have rendered many features of the software ineffective, and its lack of compatibility with newer Windows versions renders it unusable on modern systems. Furthermore, security vulnerabilities which would have been patched in more current software are highly likely to exist in this outdated program.
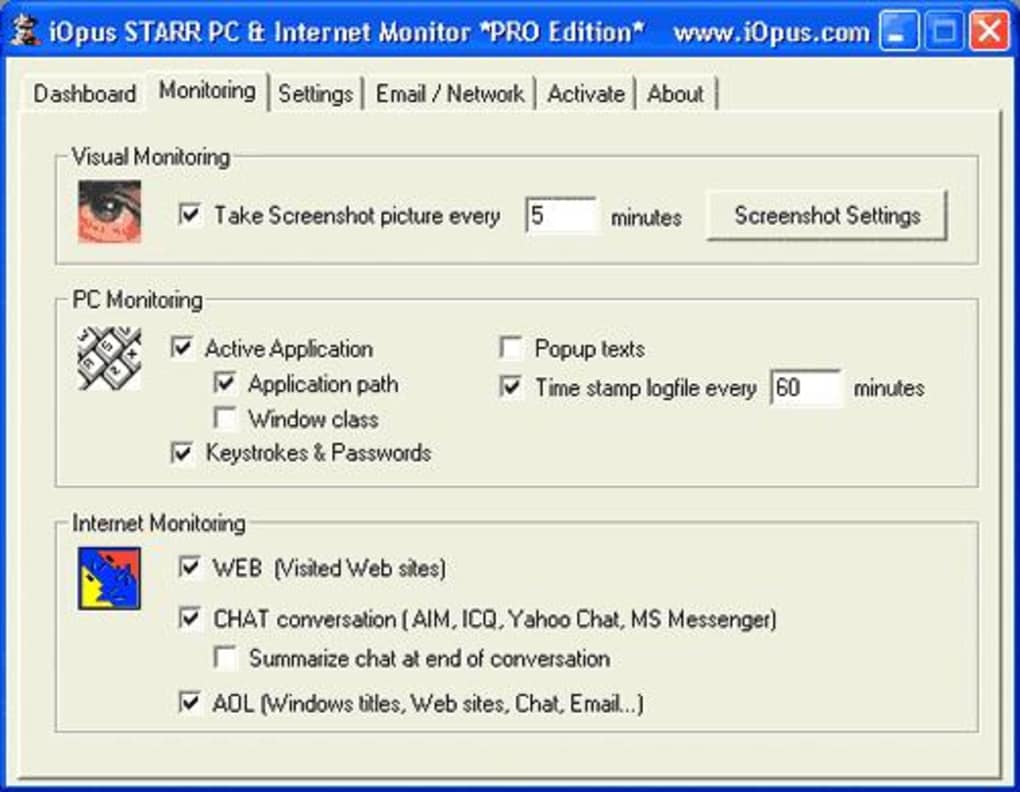
The simplicity of iOpus STARR, while a strength in its time given resource constraints, ultimately contributed to its obsolescence. Modern security software packages offer far more comprehensive features, including real-time threat detection, malware protection, firewall functionality, and advanced user management tools. These modern features are critical for protecting against the sophisticated threats that have emerged since 2005.
iOpus STARR: Comparison to Modern Security Software
Compared to modern security software, iOpus STARR’s capabilities appear rudimentary. Current applications typically integrate multiple security layers, including antivirus protection, anti-malware scanning, firewalls, intrusion detection systems, and web filtering. These functionalities are crucial in combating today’s sophisticated cyber threats, encompassing phishing attempts, ransomware attacks, and various forms of malware. Modern security software also frequently incorporates features like data encryption, password management, and VPN capabilities for enhanced online privacy and security. The user experience has also drastically improved in modern applications, with intuitive interfaces and centralized management consoles.
iOpus STARR’s absence of these crucial features highlights the vast advancements in computer security technology over the past two decades. Its historical importance lies not in its technical superiority, but rather in its contextual significance in an earlier technological landscape with different security challenges and limitations.
Conclusion
iOpus STARR serves as a fascinating glimpse into the past of computer security software. Its regional popularity and simple functionality reflected the technological and socio-political context of 2005. While its technical capabilities are significantly outdated by today’s standards, its legacy lies in providing a basic level of access control in a time when more sophisticated solutions were less accessible or less necessary for a subset of users. This historical context makes iOpus STARR a notable, albeit obsolete, piece of software history. Its story highlights the rapid pace of technological advancement in the field of computer security and underscores the importance of consistently updating software to address evolving threats. While users should avoid installing or using this outdated software, studying its historical role can offer valuable insights into the evolution of security solutions.
File Information
- License: “Trial version”
- Version: “3.27”
- Latest update: “September 22, 2005”
- Platform: “Windows”
- OS: “Windows ME”
- Language: “English”
- Downloads: “8.2K”
- Size: “1.59 MB”
















