Mimikatz, a free and open-source security auditing tool, initially designed to demonstrate vulnerabilities within the Microsoft Windows operating system, has become a widely recognized and utilized tool in both security testing and ethical hacking. While its capabilities can be misused for malicious purposes, understanding its functionality is crucial for network administrators and security professionals to effectively protect their systems. This article provides a comprehensive overview of Mimikatz, exploring its capabilities, usage, advantages, disadvantages, and its role in the broader landscape of cybersecurity.
Understanding Mimikatz’s Functionality and Purpose
Mimikatz’s core functionality revolves around extracting and manipulating Windows authentication credentials. It achieves this by leveraging vulnerabilities within the Windows security architecture, allowing access to sensitive information like Kerberos tickets, cached passwords, and other authentication tokens. This access enables privilege escalation, allowing attackers to gain elevated permissions within a system, and lateral movement across a network. Importantly, Mimikatz’s power lies not in exploiting zero-day vulnerabilities, but rather in exploiting known weaknesses and misconfigurations within the Windows environment. This makes it an incredibly effective tool for penetration testers and security professionals seeking to identify vulnerabilities before malicious actors can exploit them.
The tool’s primary use is as a powerful security auditing tool. By employing Mimikatz to test your own network, you can proactively identify vulnerabilities and weaknesses that might otherwise remain undetected. This proactive approach allows for the implementation of targeted security measures, strengthening the network’s defenses against potential attacks. The ability to simulate real-world attack scenarios enables organizations to identify and remediate potential security breaches before they can occur.
Rather than solely focusing on detecting malicious software, organizations must adopt a layered security approach. Traditional antivirus and antimalware software provides a crucial first line of defense, but sophisticated attacks often bypass these measures. Mimikatz highlights the importance of anticipating and mitigating attacks, understanding how intruders might exploit system vulnerabilities, and implementing safeguards beyond the reach of typical security software. Mimikatz offers a powerful method of simulating these advanced attacks, highlighting weak points in the system’s security architecture.
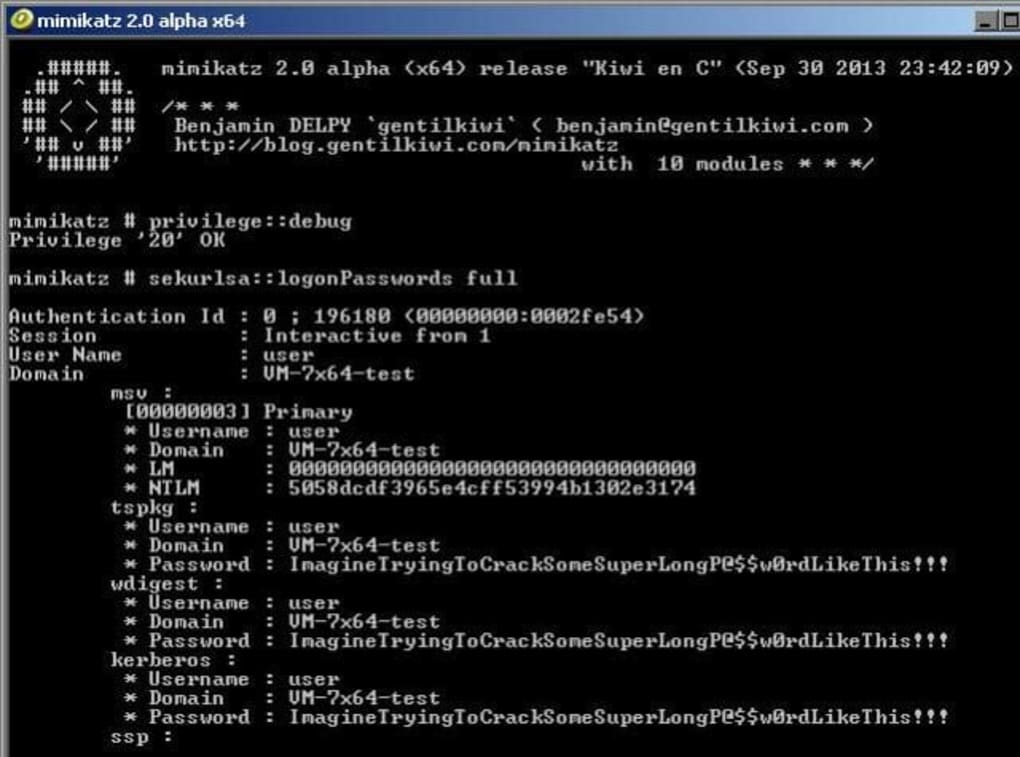
The tool’s effectiveness stems from its constant evolution. The active development and frequent updates ensure its continued relevance in the face of evolving Windows security mechanisms. The dedicated community of developers and security researchers consistently improves Mimikatz, expanding its capabilities and adapting it to address new security challenges. This active development lifecycle contributes significantly to the tool’s long-term viability and effectiveness as a penetration testing and security assessment tool.
Mimikatz: A Tool for Security Professionals and Ethical Hackers
For security professionals and penetration testers, Mimikatz represents an invaluable asset in their arsenal. By gaining firsthand experience with the tools and techniques used by malicious actors, security professionals can better understand the threats they face and develop more robust security strategies. Using Mimikatz within a controlled environment, such as a penetration testing exercise or a security audit, enables the identification of vulnerabilities that might otherwise be overlooked. This hands-on approach allows for a deeper understanding of the attack surface and facilitates the development of effective mitigation strategies.
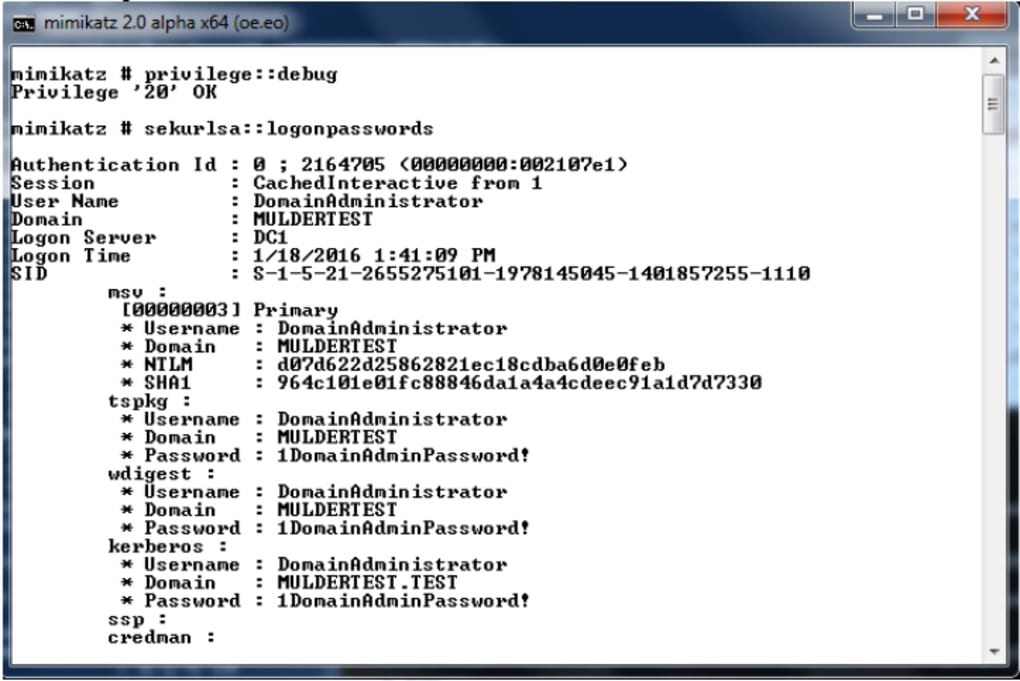
The tool’s ability to simulate various attack vectors and scenarios makes it an incredibly versatile tool for vulnerability assessments and penetration testing. By systematically testing a network’s security posture, security professionals can identify weaknesses and implement necessary countermeasures. This proactive approach to security significantly reduces the risk of successful attacks and minimizes the potential impact of security breaches.
The learning curve associated with mastering Mimikatz is undeniable. It requires a deep understanding of Windows security architecture, network protocols, and security concepts. Proficiency demands a high level of technical expertise and a solid grasp of the underlying principles of information security. However, the benefits derived from mastering this tool far outweigh the challenges faced during the learning process.
Furthermore, Mimikatz extends beyond Windows environments. While primarily associated with Windows systems, its capabilities can be adapted to other operating systems, including Mac, UNIX, and Linux. This adaptability highlights its versatility and value as a comprehensive security assessment tool applicable across various platforms. While the specifics of its implementation might vary depending on the operating system, its core functionality of credential extraction and manipulation remains a constant.
Advantages of Using Mimikatz (for Ethical Purposes):
- Proactive Security Assessment: Mimikatz allows for simulating real-world attacks, identifying vulnerabilities and strengthening network security before malicious actors can exploit them.
- Credential Extraction and Analysis: It enables the extraction and examination of authentication credentials, providing insights into potential security breaches and weaknesses.
- Privilege Escalation Testing: Mimikatz allows for testing privilege escalation vulnerabilities, determining if an attacker can gain elevated privileges within the system.
- Lateral Movement Simulation: It can be used to simulate lateral movement across a network, identifying potential pathways for attackers to move between systems.
- Windows Service Management: Mimikatz allows users to start, stop, and disable Windows services, a crucial skill in security auditing and troubleshooting.
- Bug Testing and Troubleshooting: The tool can be valuable for debugging and troubleshooting system-level issues related to authentication and access control.
- Community-Driven Development: The active development community ensures Mimikatz remains up-to-date and relevant, adapting to new security challenges.
Disadvantages of Using Mimikatz:
- Requires Advanced Technical Skills: Using Mimikatz effectively requires substantial expertise in Windows security, networking, and hacking techniques.
- Microsoft Updates: Microsoft’s continuous security updates often render specific Mimikatz techniques obsolete, requiring continuous adaptation and updating of skills and techniques.
- Time-Consuming and Resource-Intensive: Effective use of Mimikatz requires significant time, effort, and a methodical approach to analysis.
- Potential for Misuse: The powerful capabilities of Mimikatz can be easily abused for malicious purposes, emphasizing the importance of ethical and responsible use.
- Creativity and Adaptability Required: Simply using Mimikatz is insufficient; creativity and adaptability are required to overcome evolving security measures and exploit system vulnerabilities.
Conclusion: Responsible Use and Ethical Considerations
Mimikatz remains a potent tool in the cybersecurity landscape. While possessing the potential for malicious use, its primary value lies in its ability to enhance the security posture of organizations. Its utilization by ethical hackers and security professionals allows for the proactive identification and mitigation of vulnerabilities before malicious actors can exploit them. However, the ethical implications of using such a powerful tool must be clearly understood and adhered to. Responsible use requires strict adherence to legal and ethical guidelines, ensuring that the tool is only used within authorized contexts and with explicit permission. The power of Mimikatz demands responsibility and a commitment to upholding the highest ethical standards. The tool’s effectiveness in proactive security is only realized when used responsibly and ethically, reinforcing the importance of security awareness training and ethical hacking practices.
File Information
- License: “Free”
- Version: “2.2.0”
- Latest update: “July 20, 2021”
- Platform: “Windows”
- OS: “Windows 7”
- Language: “English”
- Downloads: “7.9K”
- Size: “3.00 MB”
















