Nessus, a prominent name in the cybersecurity landscape, is a powerful vulnerability scanner renowned for its comprehensive approach to identifying security weaknesses in computer systems and networks. This in-depth analysis explores the capabilities, history, and significance of Nessus within the broader context of network security. We will examine its core functionality, its place among competing vulnerability scanners, and its evolution to meet the ever-changing threatscape of modern cyberattacks.
The Core Functionality of Nessus: Beyond Traditional Scanning
Traditional network security scanners often focus solely on network services, identifying vulnerabilities based on the ports open and services running on a system. While this approach is valuable, it falls short in addressing the increasingly complex threat landscape where vulnerabilities are exploited through weaknesses in applications, operating systems, and even individual components. This is where Nessus distinguishes itself.
Nessus goes beyond simple port scanning to conduct a deep dive into the vulnerabilities present within a system, irrespective of whether they are remotely accessible or reside within the host’s local environment. It achieves this through a vast and regularly updated database of security checks, covering a broad spectrum of operating systems, applications, and network devices. This database is continuously updated, ensuring that Nessus remains current with the latest security threats and newly discovered vulnerabilities. The frequency of these updates underscores the dynamism of the cybersecurity world and Nessus’ commitment to staying ahead of the curve.
The plugin-based architecture of Nessus allows for granular control and customization. Users can select specific plugins to target particular aspects of their system or network, tailoring scans to meet specific security requirements. This flexibility ensures efficient resource utilization and avoids the potential for overwhelming the system with excessive scanning activity. The nessus-update-plugins command facilitates easy updates of this crucial plugin database, ensuring that the latest checks are readily available. Furthermore, an RSS feed provides a convenient method to track the addition of new plugins and security checks, keeping users informed about updates in real-time.
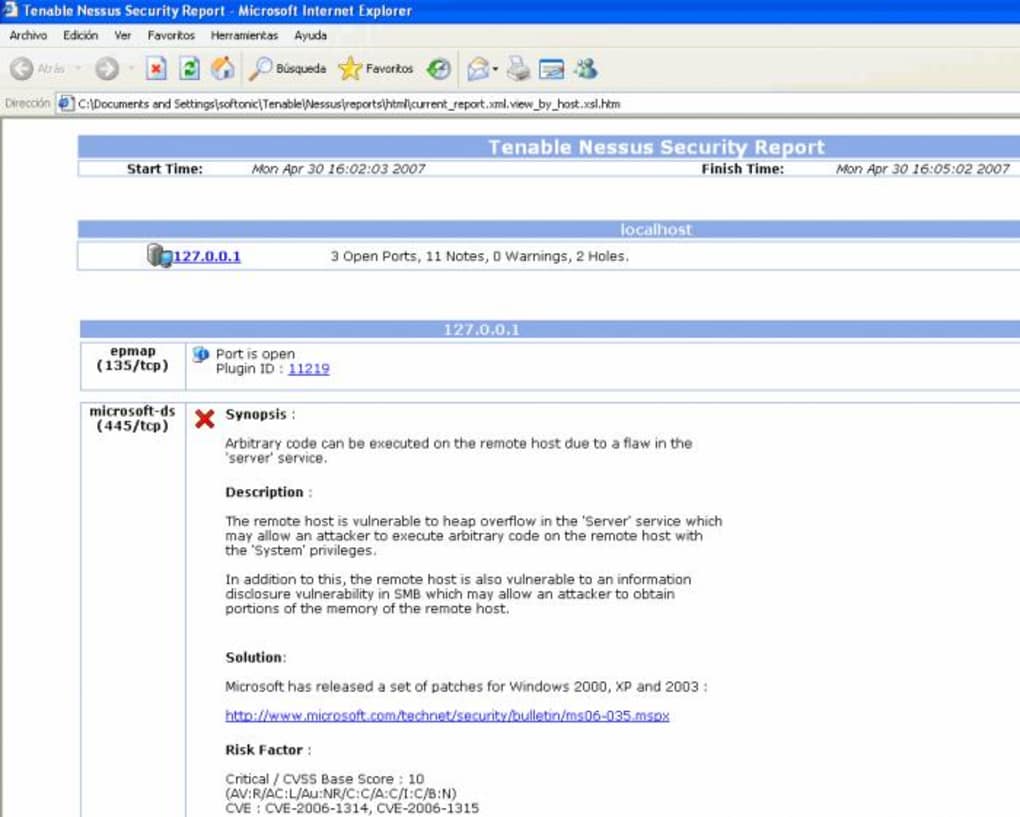
The ability to detect both remote and local vulnerabilities is a significant advantage Nessus offers. This comprehensive approach allows organizations to identify and address a wider range of vulnerabilities that might otherwise go unnoticed by traditional scanners. It recognizes that threats can originate from various sources, including network intrusions, software flaws, and misconfigurations, and addresses them accordingly. Whether the system is running Windows, macOS, or a Unix-like operating system, Nessus is equipped to provide a thorough assessment.
Nessus’s Role in a Modern Security Strategy
In today’s interconnected world, security threats are increasingly sophisticated and diverse. Traditional methods of securing networks are no longer sufficient. Nessus plays a pivotal role in a modern security strategy by providing a comprehensive and proactive approach to vulnerability management.
The ability to identify vulnerabilities before they can be exploited is critical in mitigating risk. Nessus facilitates this by offering a proactive approach to vulnerability detection. Regularly scheduled scans allow organizations to identify potential weaknesses before malicious actors can exploit them. The timely discovery of vulnerabilities is paramount to implementing effective security measures and preventing successful attacks.
Beyond identifying vulnerabilities, Nessus helps to prioritize remediation efforts. By ranking vulnerabilities based on severity, it aids security teams in efficiently addressing the most critical issues first. This prioritization ensures that resources are allocated effectively and that the most significant risks are mitigated promptly.
Nessus integrates with existing security infrastructure, including Security Information and Event Management (SIEM) systems, allowing for centralized security management and monitoring. This integration streamlines security operations, enhancing overall efficiency and reducing response times to security incidents. The reporting capabilities of Nessus further assist in tracking progress, analyzing security trends, and demonstrating compliance with relevant security regulations and standards.
Comparison with Alternative Vulnerability Scanners
The market for vulnerability scanners is competitive, with various solutions offering different capabilities and features. While Nessus excels in its comprehensive approach and extensive plugin library, understanding its position within this ecosystem is important.
Some alternative scanners focus on specific aspects of security, such as web application vulnerability assessments. Others might specialize in particular operating systems or network technologies. While these specialized scanners can be beneficial in addressing specific needs, Nessus offers a broader scope, acting as a comprehensive solution that addresses a wider range of potential security weaknesses.
The choice of a vulnerability scanner often depends on the specific needs and resources of an organization. Consider the size of the network, the complexity of the IT infrastructure, and the budget constraints when selecting a suitable solution. Nessus’s robust features and comprehensive coverage might be ideal for larger enterprises, while smaller organizations might opt for less feature-rich but more cost-effective alternatives. Regardless of the specific choice, the selection of a vulnerability scanner remains a crucial component of a robust security strategy.
The Evolution of Nessus and Future Trends
Since its inception, Nessus has undergone continuous development and improvement, adapting to the constantly changing threat landscape. Its evolution reflects the dynamic nature of cybersecurity, with new features and capabilities added to address emerging threats and enhance its overall functionality. This ongoing development ensures that Nessus remains a leading solution in the vulnerability management space.
Future trends in vulnerability scanning are likely to involve increased automation, artificial intelligence (AI), and integration with other security tools. AI-powered analysis could enhance the ability to prioritize and remediate vulnerabilities more effectively. Increased automation could streamline the scanning process, freeing up security professionals to focus on more complex tasks. Furthermore, closer integration with other security tools could enhance the overall efficacy of security operations.
Nessus is likely to play a central role in these future trends. Its continuous development and adaptability ensure it will likely remain a leading vulnerability scanner, adapting and evolving to meet the challenges of a constantly changing threat landscape. Its commitment to innovation ensures its relevance in the ever-evolving field of cybersecurity.
In conclusion, Nessus offers a robust and comprehensive approach to vulnerability scanning, surpassing the limitations of traditional methods. Its extensive plugin library, regular updates, and ability to detect both remote and local vulnerabilities make it an invaluable tool in any organization’s security strategy. As the cybersecurity landscape continues to evolve, Nessus will likely remain a cornerstone of proactive vulnerability management.
File Information
- License: “Free”
- Version: “5.0”
- Latest update: “April 30, 2007”
- Platform: “Windows”
- OS: “Windows 2003”
- Language: “English”
- Downloads: “14.6K”
- Size: “11.98 MB”
















