NetCut is a network management tool that has gained both popularity and notoriety for its capabilities. While marketed as a simple way to monitor and manage network activity, its potential for misuse has raised significant concerns. This article explores the functionalities of NetCut, its potential benefits and drawbacks, and the ethical considerations surrounding its use.
Understanding NetCut’s Core Functionalities
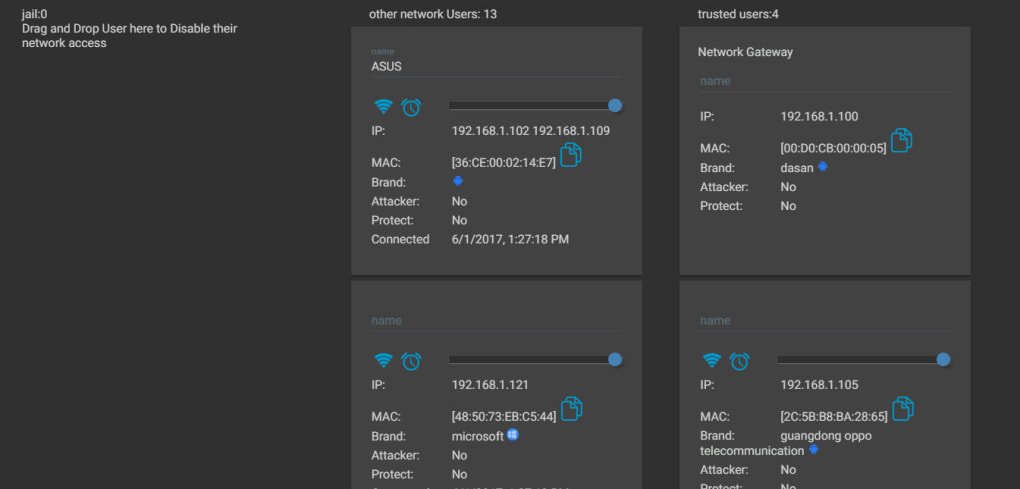
NetCut’s primary function is to provide users with a comprehensive overview of their network’s connected devices. It acts as a network scanner, identifying computers, smartphones, and other devices connected to the network via Wi-Fi or Ethernet. For each detected device, NetCut displays crucial information, including:
- IP Address: The unique numerical identifier assigned to each device on the network. This allows for precise identification and targeting of individual devices.
- Hostname: The user-friendly name assigned to the device (if available). This can provide more context than just the IP address.
- MAC Address: A unique physical address hardcoded into the device’s network interface. This identifier is crucial for device recognition, even if the IP address changes.
- Bandwidth Usage: A real-time display of the amount of network bandwidth each device is consuming. This is particularly useful for identifying devices hogging bandwidth and potentially causing network slowdowns.
- Device Status: Indicates whether a device is currently active and connected to the network. This helps users track when devices join or leave the network.
Beyond simple network scanning, NetCut offers advanced features, especially in its Pro version, that allow for more direct control over network traffic. This control extends to actions like:
- Internet Speed Control: The ability to throttle the internet speed of specific devices on the network. While useful for managing bandwidth allocation among multiple users, this functionality also raises significant ethical and legal concerns.
- MAC Address Modification: The potential to change or clone a device’s MAC address. This advanced feature has implications for network security and can be exploited for malicious purposes.
The Dual Nature of NetCut: Benefits and Risks
NetCut’s capabilities make it a powerful tool, but its potential for both legitimate and malicious use creates a complex picture. Let’s examine both sides:
Potential Benefits:
- Network Monitoring: For network administrators or home users with multiple devices, NetCut provides a valuable way to monitor bandwidth usage and identify potential network bottlenecks. Real-time monitoring allows for quick responses to performance issues.
- Troubleshooting: When network problems arise, NetCut can assist in identifying the source. By pinpointing devices with high bandwidth consumption or unusual activity, it can help diagnose and resolve issues faster.
- Security Awareness: While not a security tool itself, NetCut can raise awareness of devices connected to a network. This can be helpful in identifying unauthorized access or detecting potentially compromised machines.
- Parental Control (with caution): NetCut’s ability to control internet speed could be used as a rudimentary form of parental control. However, it’s crucial to use this feature responsibly and ethically, ensuring transparency and avoiding abusive practices.
Potential Risks and Ethical Concerns:
- Unauthorized Access and Interference: The ability to throttle internet speeds or modify MAC addresses poses a significant risk. Malicious users could disrupt network services for other users, creating denial-of-service situations.
- Privacy Violations: Monitoring bandwidth usage without consent raises serious privacy concerns. NetCut’s capacity to track which websites or services a device is accessing could be used for surveillance, violating individuals’ privacy.
- Misuse and Abuse: NetCut’s features can be misused for cyberbullying, harassment, or other malicious activities. Controlling someone’s internet access without their knowledge or consent is unethical and potentially illegal.
- Legal Ramifications: The legality of using NetCut’s advanced features varies by jurisdiction. Unauthorized network interference or access can lead to serious legal consequences, including fines or criminal charges.
NetCut Defender and Network Security
NetCut comes with a component called NetCut Defender, which aims to provide protection against intrusion attempts. This feature essentially works as a countermeasure against other instances of NetCut attempting to modify network settings or access the system. While it’s designed to bolster security, it’s important to understand its limitations. NetCut Defender cannot fully protect against sophisticated attacks, and a determined attacker could still find ways to bypass it.
The presence of NetCut Defender highlights a key aspect of network security: it’s a multifaceted issue, not solely solved by a single tool. Relying solely on NetCut Defender to protect against malicious activity is a risky approach. A comprehensive security strategy involves multiple layers of protection, including strong passwords, firewalls, and regular software updates.
Alternatives to NetCut and Responsible Network Management
Several alternative network management tools exist, offering comparable functionality with potentially reduced risks. Many are open-source, allowing for greater transparency and community scrutiny. These alternatives often focus on network monitoring and diagnostics rather than offering control over individual devices’ internet access.
Choosing a responsible alternative is crucial for ethical and legal compliance. This also emphasizes the importance of practicing responsible network management. Open communication within a shared network is crucial. Clear expectations about acceptable bandwidth usage and network access should be established, fostering a more collaborative and respectful online environment.
Conclusion: Harnessing the Power Responsibly
NetCut, with its powerful features, presents a double-edged sword. While its network monitoring capabilities can be beneficial for managing and troubleshooting network issues, its potential for misuse creates considerable ethical and legal concerns. The ability to manipulate network traffic and control internet access should be approached with extreme caution. Users need to be aware of the potential for abuse and the legal repercussions of unauthorized network interference.
Instead of relying on tools that enable control over other users’ connections, focusing on responsible network practices, clear communication, and secure network configurations is essential. Adopting a proactive approach to security and prioritizing the ethical use of technology creates a safer and more respectful online environment for everyone. Choosing alternative network management tools that prioritize monitoring and diagnostics over control reduces the risks associated with potentially harmful actions. Ultimately, responsible network management requires a combination of effective tools and a strong commitment to ethical conduct.
File Information
- License: “Free”
- Version: “3.0.138”
- Latest update: “July 15, 2022”
- Platform: “Windows”
- OS: “Windows 7”
- Language: “English”
- Downloads: “34.6K”
- Size: “4.57 MB”
















