Perimeter 81 is a cloud-native network security platform designed for businesses of all sizes. It offers a unified approach to managing network security, simplifying complex tasks and providing robust protection against modern cyber threats. This comprehensive review delves into the platform’s features, benefits, and drawbacks, providing a clear picture of its suitability for different organizations.
Enterprise-Grade Security with User-Friendly Simplicity
Perimeter 81 stands out for its ability to blend robust, enterprise-grade security with an intuitive user interface. Unlike many traditional security solutions that require extensive technical expertise to configure and manage, Perimeter 81 prioritizes ease of use. The platform’s cloud-based architecture eliminates the need for on-premise hardware and complex configurations, enabling rapid deployment and streamlined management. This translates to significant cost savings in terms of hardware acquisition, maintenance, and IT personnel time.
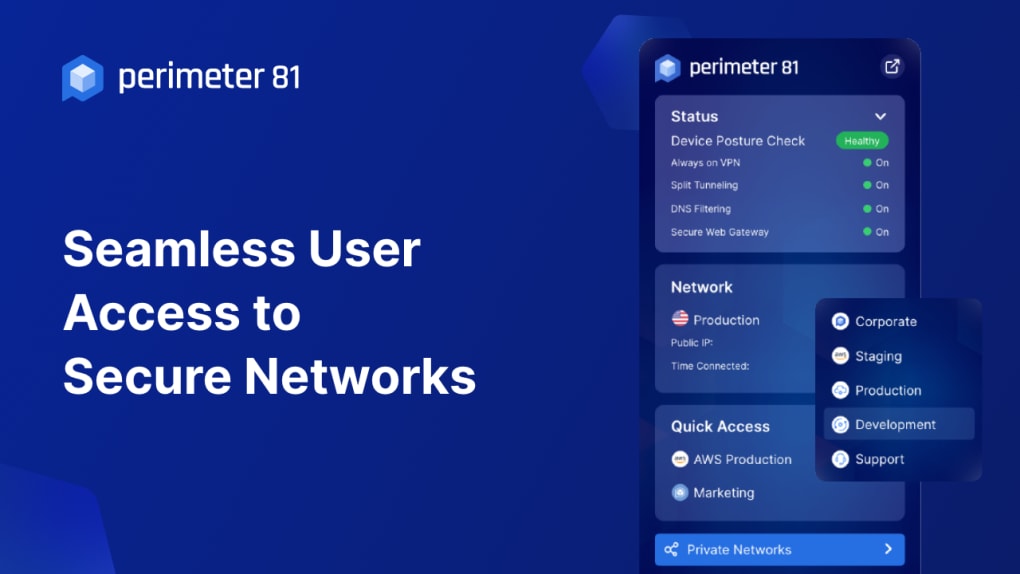
The core of Perimeter 81’s security lies in its implementation of Zero Trust Network Access (ZTNA). This fundamental security principle dictates that no user or device should be implicitly trusted, regardless of location. Every access request is meticulously verified before granting permission, significantly reducing the attack surface and mitigating the risks associated with unauthorized access. ZTNA is complemented by a comprehensive suite of security tools, including:
-
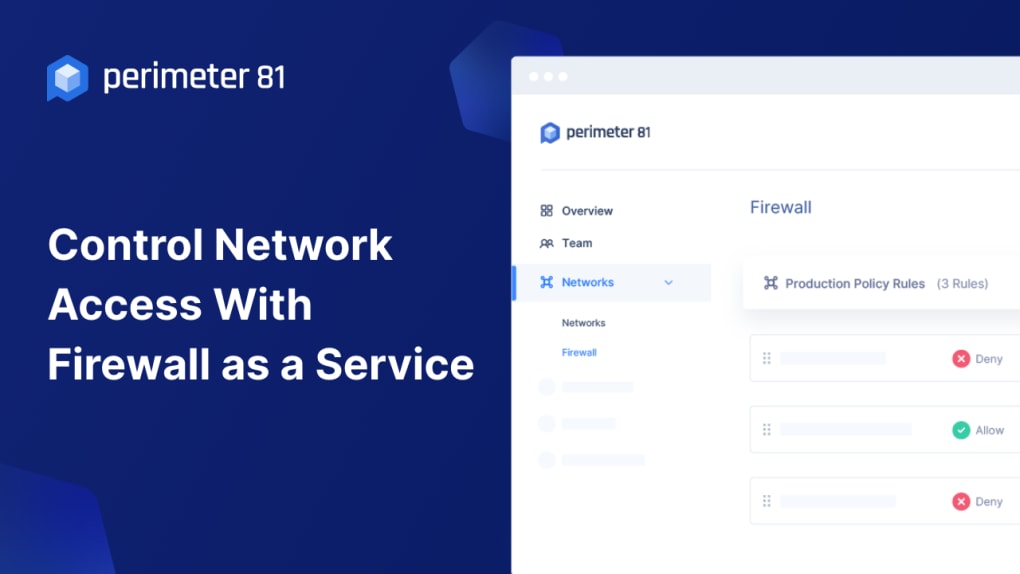
Firewall as a Service (FWaaS): Perimeter 81’s FWaaS acts as a virtual firewall, inspecting and filtering network traffic to prevent malicious access attempts and data breaches. This cloud-based firewall dynamically adapts to evolving threats, ensuring consistent protection without the need for manual updates and configurations.
-
Web Filtering and Malware Protection: These integrated tools safeguard users from malicious websites and malware downloads. Administrators can define customized policies to control access to specific websites and applications, ensuring compliance with corporate policies and mitigating the risks of employees inadvertently accessing harmful content or downloading malware. This layer of protection proactively identifies and blocks threats, preventing them from impacting the network and compromising sensitive data.
- Dedicated Static IP Addresses and Network Segmentation: Perimeter 81 allows businesses to create multiple virtual networks, each with its own dedicated static IP addresses. This capability enables granular control over network access, enabling administrators to segment sensitive resources and limit access based on roles and responsibilities. This approach reduces the blast radius of potential security breaches, minimizing the impact of a compromised account or device.
Global Reach and Seamless Connectivity
Perimeter 81 boasts a global network of over 50 Points of Presence (PoPs) strategically located around the world. This extensive network infrastructure ensures low-latency connections and optimal performance for users regardless of their geographical location. Whether employees are working from the office, remotely from home, or traveling internationally, they can expect a consistent and reliable connection to corporate resources. This global reach is crucial for businesses with geographically dispersed teams or international operations, ensuring secure and efficient connectivity for all users. The platform’s seamless integration with various devices and operating systems further enhances accessibility and convenience for employees.
Centralized Management and Simplified Administration
The platform’s unified management console simplifies administration and reduces the burden on IT teams. All aspects of the network security infrastructure can be managed from a single pane of glass, eliminating the need to juggle multiple tools and consoles. This centralized approach streamlines troubleshooting, reduces operational complexity, and improves overall efficiency.
Furthermore, Perimeter 81 handles all updates and patches automatically, eliminating the need for manual intervention and reducing the risk of security vulnerabilities. This automated approach frees up IT staff to focus on more strategic initiatives rather than routine maintenance tasks. The platform’s comprehensive reporting and analytics tools provide valuable insights into network activity, enabling proactive identification and mitigation of potential security threats.
Exceptional Support and Training
Perimeter 81 provides comprehensive support and training resources to its customers. A dedicated support team is available 24/7 to assist with any technical issues or queries. This commitment to customer support ensures that businesses can rely on Perimeter 81’s expertise to address any challenges they may encounter. The platform also offers extensive training materials to help users fully leverage its capabilities and optimize their security posture. This comprehensive approach to support and training ensures that businesses can maximize the value of their investment in Perimeter 81.
Cost-Effectiveness and Scalability
While Perimeter 81 is a premium solution, its cloud-based architecture and streamlined management contribute to cost-effectiveness in the long run. The elimination of on-premise hardware, reduced IT management overhead, and improved security posture contribute to significant cost savings. Moreover, the platform’s scalability allows businesses to adapt their security infrastructure to meet their evolving needs. As a business grows, adding users, devices, and networks is a straightforward process, ensuring that security remains robust and aligned with business requirements.
Addressing Potential Drawbacks
While Perimeter 81 offers numerous benefits, it’s essential to acknowledge potential drawbacks. Some users have reported a slight learning curve during initial setup and configuration. However, the platform’s intuitive interface and comprehensive documentation largely mitigate this issue. Furthermore, the platform’s reliance on a cloud-based infrastructure might raise concerns regarding data sovereignty and compliance for businesses operating in highly regulated industries. However, Perimeter 81 offers a range of compliance certifications and configurable settings to address these concerns.
Another potential concern is the cost associated with the premium service. While the long-term cost savings can be significant, businesses need to carefully consider their budget and evaluate the return on investment before committing to the platform. A thorough assessment of existing security infrastructure and future needs is crucial to determine the optimal solution for a specific organization.
Conclusion: A Powerful Solution for Modern Businesses
Perimeter 81 presents a compelling solution for businesses seeking a robust, yet user-friendly, network security platform. Its cloud-based architecture, unified management capabilities, and comprehensive suite of security tools make it an attractive option for organizations of all sizes. While a slight learning curve and cost considerations exist, the platform’s long-term benefits in terms of improved security, simplified management, and cost efficiency outweigh these minor drawbacks. The platform’s global reach and exceptional customer support further strengthen its position as a powerful solution for businesses navigating the complexities of the modern cybersecurity landscape. For businesses seeking a seamless, secure, and efficient way to manage their network security, Perimeter 81 deserves serious consideration.
File Information
- License: “Full”
- Version: “9.0.0.16”
- Latest update: “September 14, 2023”
- Platform: “Windows”
- OS: “Windows 8.1”
- Language: “English”
- Downloads: “1.2K”
















