XArp is a security application designed to detect and mitigate Address Resolution Protocol (ARP) spoofing attacks. These attacks, often undetectable by standard firewalls and operating system security features, pose a significant threat to network security and data privacy. By employing advanced detection techniques, XArp provides a crucial layer of protection against ARP-based intrusions, safeguarding sensitive information transmitted over your network. This in-depth article explores the functionality, significance, and implications of XArp in the context of modern network security.
Understanding ARP Spoofing Attacks: A Stealthy Threat
The Address Resolution Protocol (ARP) is a fundamental network protocol that maps IP addresses to physical MAC addresses. This process is crucial for communication on local area networks (LANs). When a device needs to send data to another device on the same network, it uses ARP to determine the target device’s MAC address. This MAC address is then used to transmit the data frame.
ARP spoofing exploits this process by sending falsified ARP packets to the network. These packets claim that the attacker’s MAC address corresponds to the IP address of a legitimate device, often the network gateway or another crucial system. This deception allows the attacker to intercept all communication between the targeted device and the rest of the network.
The insidious nature of ARP spoofing lies in its ability to remain undetected by conventional security measures. Firewalls, primarily designed to filter network traffic based on IP addresses and ports, are ineffective against ARP attacks because these attacks operate at a lower level of the network stack. Similarly, operating system security features typically focus on higher-level threats, leaving ARP spoofing vulnerabilities largely unaddressed.
The consequences of a successful ARP spoofing attack can be severe. Attackers can:
- Eavesdrop on network traffic: All data transmitted between the targeted device and the network, including sensitive information like login credentials, emails, financial transactions, and confidential documents, can be intercepted.
- Manipulate network traffic: The attacker can modify or inject data into the network traffic, potentially leading to data corruption, denial-of-service attacks, or the installation of malware.
- Launch man-in-the-middle attacks: The attacker can position themselves between the targeted device and other network resources, intercepting and manipulating communications.
- Conduct session hijacking: By capturing login credentials or session cookies, the attacker can gain unauthorized access to the targeted device and its associated accounts.
The subtlety and potential impact of ARP spoofing attacks underscore the need for robust security measures specifically designed to address this vulnerability. XArp aims to fulfill this need by providing advanced ARP spoofing detection capabilities.
XArp: A Proactive Defense Against ARP Spoofing
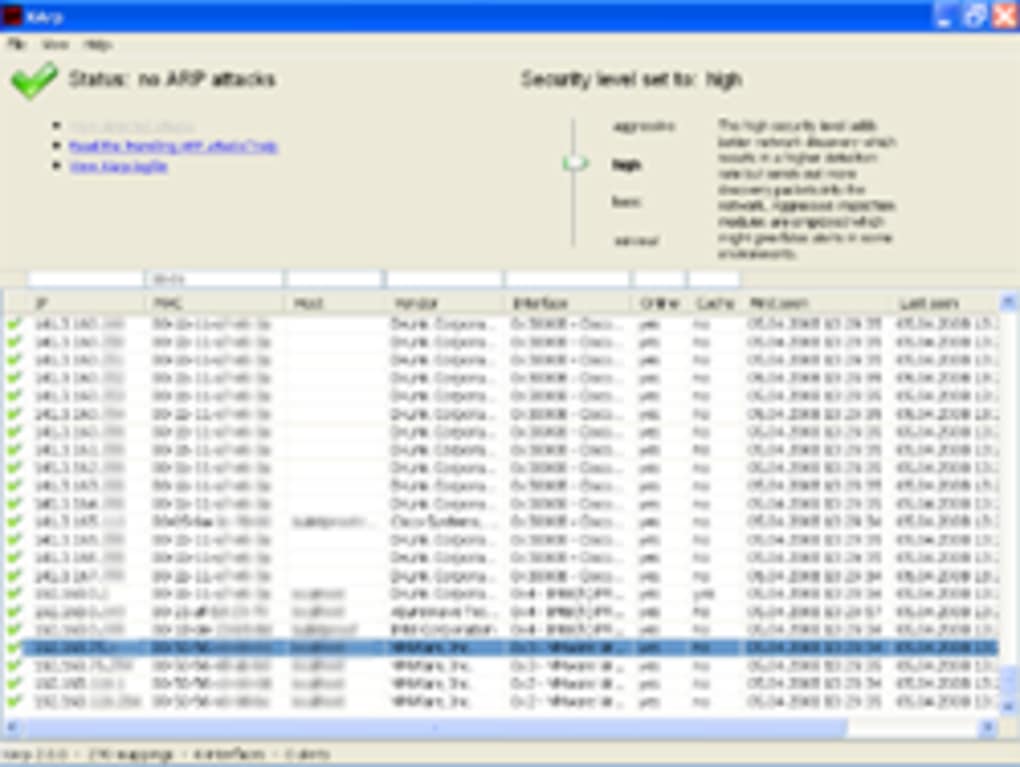
XArp stands out as a dedicated security application focusing exclusively on detecting and mitigating ARP spoofing attacks. Unlike generic security suites that may offer partial protection against ARP attacks as a secondary feature, XArp is built from the ground up to address this specific threat vector. Its effectiveness stems from its advanced detection algorithms, which continuously monitor network traffic for signs of ARP spoofing activity.
The core functionality of XArp revolves around the real-time analysis of ARP packets. The application meticulously examines each ARP packet, comparing its contents against a set of predefined rules and heuristics to identify potential signs of malicious activity. These rules and heuristics are designed to detect various ARP spoofing techniques, ensuring comprehensive protection against a wide range of attacks. The program’s detection engine constantly scans for irregularities, such as:
- Duplicate MAC addresses: If multiple devices claim the same MAC address, it could indicate an ARP spoofing attempt.
- Unexpected ARP requests: Uncommon or suspiciously frequent ARP requests can signal an attempt to flood the network or disrupt communication.
- Spoofed MAC addresses: The program compares reported MAC addresses to a database of known addresses, identifying any discrepancies.
- IP address conflicts: If multiple devices claim the same IP address, it could indicate a spoofing attempt.
Upon detecting a potential ARP spoofing attack, XArp alerts the user, providing information about the suspected attacker’s IP address and MAC address. This early warning system allows users to take immediate action to mitigate the threat, potentially preventing significant data breaches or other security incidents. The program’s design prioritizes timely alerts, minimizing the window of vulnerability.
XArp’s Technical Approach and Advantages
The effectiveness of XArp hinges on several technical aspects:
- Real-time monitoring: Continuous network monitoring ensures prompt detection of ARP spoofing attempts, allowing for immediate response.
- Heuristic analysis: XArp doesn’t rely solely on signature-based detection. Heuristic analysis enables the detection of novel and previously unseen ARP spoofing techniques.
- Low system resource usage: XArp is designed to operate with minimal impact on system performance, ensuring smooth functioning even on less powerful machines.
- User-friendly interface: The intuitive interface allows users of all skill levels to easily understand and manage the program’s settings.
Compared to other security solutions, XArp offers several key advantages:
- Dedicated ARP spoofing protection: Unlike general-purpose security software, XArp focuses solely on ARP spoofing, providing specialized and highly effective protection.
- Proactive detection: XArp proactively monitors the network for potential threats, preventing attacks before they cause significant damage.
- Early warning system: The real-time alerting system allows users to take immediate action, mitigating the impact of attacks.
- Simplicity and ease of use: XArp is designed for ease of use, even for non-technical users.
Limitations and Considerations
While XArp offers a robust solution for ARP spoofing detection, it’s crucial to acknowledge its limitations:
- Limited scope: XArp primarily focuses on ARP spoofing; it does not offer comprehensive protection against all types of network attacks. This necessitates the use of other security tools to address other vulnerabilities.
- Dependence on network configuration: The effectiveness of XArp can be influenced by the specific network configuration. In complex network environments, additional configurations might be necessary to ensure optimal performance.
- Potential for false positives: While XArp strives for accuracy, there’s a possibility of false positives, where legitimate network activity is mistakenly flagged as malicious. Regular review of alerts is advised.
- Software updates: Maintaining an up-to-date version of XArp is essential to benefit from the latest security patches and detection improvements.
Conclusion: XArp as a Critical Component of Network Security
In the ever-evolving landscape of cyber threats, ARP spoofing remains a potent and often overlooked attack vector. XArp’s specialized approach offers a valuable layer of defense against this insidious threat. Its real-time monitoring, heuristic analysis, and timely alerting capabilities combine to provide users with proactive protection against ARP-based attacks. While not a standalone solution for complete network security, XArp constitutes a critical component of a comprehensive security strategy, contributing significantly to the overall protection of sensitive data and network infrastructure. Its ease of use and dedicated focus on a specific threat make it a valuable tool for both home users and smaller businesses seeking to strengthen their network security posture.
File Information
- License: “Free”
- Version: “2.2.2”
- Latest update: “February 19, 2014”
- Platform: “Windows”
- OS: “Windows XP”
- Language: “English”
- Downloads: “21.6K”
- Size: “4.29 MB”
















